bacdoor installation to bactrack,,,,,
bacdoor installation to ubuntu,,,
pemasnagn bacdoor this time, simply by listing due to go into the application is not successful,,,,,
using tools chymothoa,,,,
when using the tool can only do cymothoa listing due to go into linux preformance can not,,,,,,,, I need help,,,,
after an analysis occurs
command axu,,,
result in permanent ijek ijek dat D in bactrak,,,,
Senin, 30 Januari 2012
CRACKING PASSWORD john the ripper
in the discussion this time was berhasila cuman crack passwords have to wait a verysurvived,,
initial use is shown in the figure below,,,
step further by including Scribe,,,,,,
in the above process is running very long,,, and will take a long time,,,,
but the process or steps are correct,,,,
good luck
initial use is shown in the figure below,,,
step further by including Scribe,,,,,,
in the above process is running very long,,, and will take a long time,,,,
but the process or steps are correct,,,,
good luck
PRIVILAGE ESCALATION
nmap in this we can see the hosts and open ports,,,,
in an open ssh port 2 op2, port 80 open http,139 open http,serta netbios-ssn open,,,
if in the open through a mantra,,
if in the open through znmap meal will be seen so what is in use and what type of kernel,,
then see which ports are open and can be attacked,,,
next to see the level and target weaknesses,,,,,
then see which ports are open,,,,znmap
The next step leading to nessus,,,,,,,
do scanning ip address,,,
The next target will see the strength in attack,,,,,,
sorry for the explanation nessus,, is less clear because the information is reduced,,,
then enter into exploitdb, to start attacking,,,
early stages of attack over ssh because ssh port open,,,,and then look at the db,,,,
then enter into wpadmin,,,, if there is any writing of eating will happen,,,
if true,,,,
then enter the command, as below,,
The next will come the results,,,,
The next will appear from the results exploid,, which is visible to the user and passwordscracker will be on the next page,,,,,,,,,, bahasas
,,,,,,,good luck,,,,,,,,,,,,,
in an open ssh port 2 op2, port 80 open http,139 open http,serta netbios-ssn open,,,
if in the open through a mantra,,
if in the open through znmap meal will be seen so what is in use and what type of kernel,,
then see which ports are open and can be attacked,,,
next to see the level and target weaknesses,,,,,
then see which ports are open,,,,znmap
The next step leading to nessus,,,,,,,
do scanning ip address,,,
The next target will see the strength in attack,,,,,,
sorry for the explanation nessus,, is less clear because the information is reduced,,,
then enter into exploitdb, to start attacking,,,
early stages of attack over ssh because ssh port open,,,,and then look at the db,,,,
then enter into wpadmin,,,, if there is any writing of eating will happen,,,
if true,,,,
then enter the command, as below,,
The next will come the results,,,,
The next will appear from the results exploid,, which is visible to the user and passwordscracker will be on the next page,,,,,,,,,, bahasas
,,,,,,,good luck,,,,,,,,,,,,,
Jumat, 27 Januari 2012
exploitation windows using metasploit
information gethering
before starting exploitation there are some things to watch,,,
select the right way virtualbox windows xp,,, and then turn off the firewall on the windows,,
then enter into nessus,,
The next view report,,,,
then see the results as well as the power level,,,,,,,
then select the targets to be attacked,,,,
The next target will be attacked there,,, then to attack,,,,,,
The next attack metasploit exploit with tools,,,,,
with scribe use windows/smb/ms08_067_netapi
input
db finally broken windows with Scribe msf exploit(ms08_067_netapi) > exploit
c in the windows system already mastered,,,,,
next try to make a folder in windows,,,,,
sintak c:\>mkdir coba buat
system in windows already in control,,,,
.............good luck................................
before starting exploitation there are some things to watch,,,
select the right way virtualbox windows xp,,, and then turn off the firewall on the windows,,
then enter into nessus,,
The next view report,,,,
then see the results as well as the power level,,,,,,,
then select the targets to be attacked,,,,
The next target will be attacked there,,, then to attack,,,,,,
The next attack metasploit exploit with tools,,,,,
with scribe use windows/smb/ms08_067_netapi
input
set payload windows/meterpreter/bind_tcp
set lhost 192.168.56.24 (target)
msf exploit(ms08_067_netapi) > exploit
db finally broken windows with Scribe msf exploit(ms08_067_netapi) > exploit
c in the windows system already mastered,,,,,
next try to make a folder in windows,,,,,
sintak c:\>mkdir coba buat
system in windows already in control,,,,
.............good luck................................
search vurnerability db windows
attacking a lan network with tools exploitdb directori,,,,with scribe
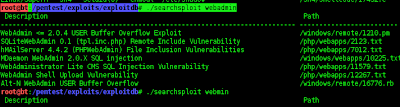
root@bt:pentest/exploits/exploitdb#./serchsploit ssh in use to interact,,,
The next step to find out db in use scribe,,
root@bt:pentest/exploits/exploitdb#./serchsploit db
to see if there are flaws in the use scribe,,,,,,
root@bt:pentest/exploits/exploitdb#./serchsploit db/platforms/windows/dos# cat14067 py
target is the db windows,,,
bove the target has not been able to enter the db windows,, good luck...,,,,,,
root@bt:pentest/exploits/exploitdb#./serchsploit ssh in use to interact,,,
The next step to find out db in use scribe,,
root@bt:pentest/exploits/exploitdb#./serchsploit db
to see if there are flaws in the use scribe,,,,,,
root@bt:pentest/exploits/exploitdb#./serchsploit db/platforms/windows/dos# cat14067 py
target is the db windows,,,
bove the target has not been able to enter the db windows,, good luck...,,,,,,
process and how the use of nessus nessus and Vulnerability
early use of nessus
open a browser and enter localhost
then enter,,,
after Enter
then log
Then click on the scan and then enter a name, select your internal network
and enter the address ipaddress,,, then press enter
results seen in the picture below,,,
The next display will appear low,high,medium,,,
The next host will HOST,protocol, svc name,,,
The next election will be the target of attack, and security level,,,
further analyze live and blamed the empty target,,,,
targets to be attacked we must know the weakness reproach targer
good luck,,,,,,
Rabu, 25 Januari 2012
instalation Nessus
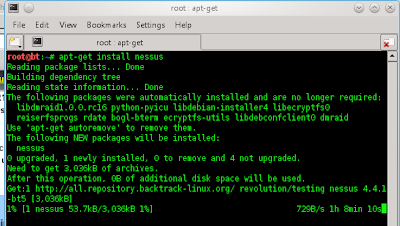
To install Nessus on Backtrack 5R1 :
apt-get install nessus like this
apt-get install nessus like this
Wait download and install till finnish like this
After installation success go to registration for nessus
Go to Backtrack Menu > Vulnerability Assessment > Vulnerability Scanner > Nessus > Nessus Register
Browser will open with url http://www.nessus.org/products/nessus/nessus-plugins/obtain-an-activation-code
Enter to Nessus use for "Home" to get activate code
Click "Agree" and fill regitsration till finnish and back to terminal type /opt/nessus/sbin/nessus-adduser
fill your login and password
Type nessus start in terminal and starting nessus and open mail used for registration nessus for information about registration nessus
Type in terminal /opt/nessus/bin/nessus-fetch --register <registration number> to activate nessus
Open browser and go to https://localhost:8834/ to enterance Nessus GUI
Login with user has added before and enterance to nessus GUI
Installation and registration is finish
good lock,,,,,,,,,,,,,,
information getring web......
to find out ipadress Spentera.com.dojo.net I use tools
root@bt:/pentest/enumeration/dns/dnsenum# ./dnsenum.pl www.Spentera.com
root@bt:/pentest/enumeration/dns/dnsenum# ./dnsenum.pl www.Spentera.com
mengunakan tools Zenmap
root@bt:/pentest/enumeration/dns/dnsenum# ./dnsenum.pl www.is2c.com
root@bt:/pentest/enumeration/dns/dnsenum# ./dnsenum.pl www.is2c.dojo.net
good luck,,,,,,,,,,,,,,,,,,,,
information gathering
Gathering information using tools
using tools nmap
- root@bt:~# nmap 192.268.0.0/24
use to search for a connected network in the local host
using tools nmap
- root@bt:~# nmap 192.268.0.0/24
use to search for a connected network in the local host
using tools Zenm ap
- how the system works right, and the graph can be seen,,
-with the command bleak look at the picture below
using tools whatweb
root@bt:/pentest/enumeration/web/whatweb# ./whatweb -v 192.168.0.44
to see the network is online.
tools are in use in accordance with the needs,,
good luck,,
good luck,,
Langganan:
Komentar (Atom)